Quick Summary: Are you ready to face the evolving landscape of cyber threats in 2026? Our blog reveals the top 10 cybersecurity trends you need to know to stay ahead of the game. Don't let cyber threats catch you off. Keep yourself updated about the cybersecurity tools and their importance to protect your organization from the latest attacks. Learn from recent attacks and stay one step ahead.
Cybersecurity trends are transforming how businesses protect their data in an increasingly connected digital landscape.
As organizations embrace cloud computing, remote work, IoT, and AI-driven systems, the surface area for cyber threats has expanded dramatically. Traditional security models are no longer enough. Sophisticated ransomware, phishing attacks, and supply chain breaches now require adaptive, intelligence-led strategies. In response, businesses are shifting their focus to proactive cybersecurity frameworks, emerging technologies, and smarter authentication methods—supported by more advanced cybersecurity tools.
The surge in cyber threats has made cybersecurity a boardroom priority. As organizations battle rising incidents of data breaches, ransomware, and insider attacks, the global cybersecurity market continues its rapid expansion. The global cybersecurity market was valued at USD 172.24 billion in 2023 and is expected to reach a staggering USD 562.72 billion by 2032, reflecting a strong compound annual growth rate (CAGR) of 14.3%. The growing market surge reflects a clear shift—businesses are not just reacting to threats; they’re proactively embracing new cybersecurity trends to safeguard their digital future.
This article explores the top cybersecurity trends driving this transformation—and how they’re helping organizations stay resilient in the face of evolving digital threats.
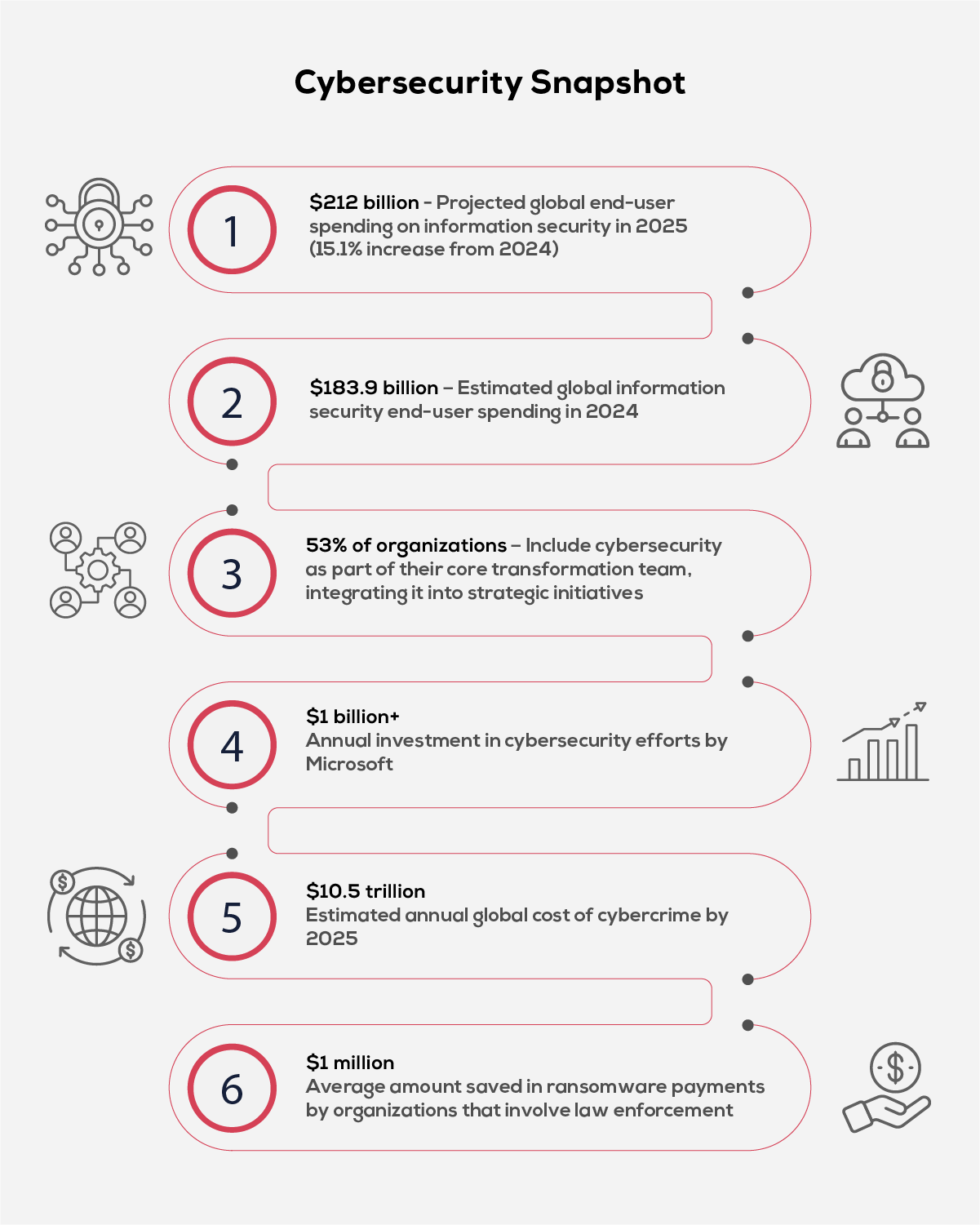
Top Cybersecurity Trends
As technology evolves, so do the tactics of cyber attackers—making it essential for organizations to stay ahead. Here are the top cybersecurity trends reshaping the way businesses safeguard their digital assets

1. Smarter Security with AI / ML
Artificial intelligence is no longer just an enabler—it’s fast becoming the backbone of modern cybersecurity. With the rise of Generative AI and advanced machine learning models, security systems are evolving from static rule-based frameworks to dynamic, self-learning ecosystems. These technologies can anticipate threats before they strike, analyze behavioral patterns at scale, and neutralize risks with minimal human intervention.
From detecting abnormal login behavior to filtering out AI-generated phishing content, GenAI and ML are enhancing precision, speed, and decision-making in security operations. As cyber threats grow more complex, this trend signals a shift toward predictive, autonomous defense strategies that can adapt in real time.
2. Proactive Threat Hunting & Detection Engineering
As cyberattacks grow more evasive, the emphasis is shifting from reactive defense to proactive detection. Threat hunting—a practice driven by human intuition, behavioral analysis, and investigative curiosity—is becoming an essential part of modern security operations. It combines manual expertise with automation to identify subtle threats that evade traditional tools. But beyond just finding threats, its true value lies in sharpening long-term defenses.
This is where detection engineering steps in—an emerging discipline focused on building and refining detection logic within security systems. By continuously tuning alert rules, leveraging threat intelligence, and optimizing SIEM/SOAR tools, detection engineers help turn isolated incidents into lasting improvements.
3. Adaptive Zero Trust Architecture
Zero Trust Security, outlined in the Cybersecurity and Infrastructure Security Agency’s (CISA) Zero Trust Maturity Model, is being adopted by more organizations to strengthen access control. Based on the principle of “never trust, always verify,” it treats every access request as a potential risk—whether it comes from inside or outside the network. By verifying user identities and restricting access to only what’s necessary, it helps reduce the chances of internal movement during a breach.
As remote work and cloud services become common, Zero Trust provides a practical model to secure distributed systems. It helps organizations maintain control over who accesses what, reduce the impact of a breach, and improve their ability to respond to threats.
4. Data-Centric Security Practices
Cybersecurity is becoming increasingly data-driven—but more data doesn't always mean better protection. The real shift lies in prioritizing high-quality, well-governed data to power smarter detection, accurate threat modeling, and effective automation.
Poor data quality—whether it's incomplete, outdated, or inconsistent—can lead to false positives, missed threats, or flawed decision-making. That’s why organizations are now placing greater emphasis on data accuracy, integrity, and privacy across all security operations. This trend reflects a broader movement toward treating data as a security asset, not just an input.
5. Unified Access with Single-Vendor SASE
As hybrid work becomes the norm, enterprises are adopting single-vendor SASE solutions to simplify security and ensure high-performance access for users—wherever they work. By combining networking and security in one cloud-delivered platform, SASE reduces complexity while maintaining speed, reliability, and data protection.
This approach enables consistent access to SaaS and cloud applications with minimal latency, even across remote or mobile work environments. With fewer integration points and centralized control, single-vendor SASE offers the agility and security today’s distributed workforce demands.
6. New Solutions to Bridge the Cyber Talent Gap
The global shortage of cybersecurity talent remains a pressing concern for both the public and private sectors. To address this, organizations are adopting creative strategies that go beyond traditional hiring. AI-powered copilots are emerging as digital allies, helping cybersecurity teams automate routine tasks, analyze threats faster, and access real-time insights—allowing professionals to focus on higher-value work with greater efficiency.
At the same time, governments and institutions are investing in student-powered Security Operations Centers (SOCs). These collaborative environments give students hands-on experience while supporting critical threat monitoring for public agencies. Together, AI copilots and academic partnerships are helping fill critical workforce gaps, equipping the next generation while empowering today’s teams to meet rising security demands.
7. Integrated Security for 5G and IoT Systems
Governments around the world are accelerating efforts to modernize public infrastructure with built-in security as a priority. This includes upgrading legacy systems and adopting smart technologies that support digital services across transportation, energy, and city management. Investments in 5G networks, AI-driven monitoring, and connected devices are forming the foundation of secure, efficient, and citizen-focused infrastructure.
To ensure these systems operate reliably, agencies are deploying integrated security solutions designed for complex environments. From ruggedized hardware in remote locations to real-time visibility across IoT and OT networks, these tools help maintain operational continuity while safeguarding sensitive data and services. Security is no longer an afterthought—it’s becoming an essential layer of every digital infrastructure initiative.
8. Smarter Authentication with Biometrics and Passkeys
Authentication is evolving from static passwords to more intelligent, identity-driven methods. Organizations are increasingly adopting passwordless technologies such as passkeys, fingerprint recognition, and facial screening to streamline secure access. These methods not only reduce friction for users but also strengthen authentication by tying it to physical or biometric identifiers that are harder to replicate.
In parallel, behavioral biometrics—which analyzes patterns like keystroke dynamics, mouse movement, or device interaction—is gaining traction as an added layer of verification. Combined with physical biometrics, these methods create a more adaptive and continuous authentication experience. As adoption grows, enterprises are aligning these advancements with their security frameworks to ensure seamless, context-aware access across applications and devices.
9. Strategic Cloud Security Prioritization
As cloud adoption accelerates, enterprises are placing greater emphasis on strengthening their cloud security posture. This involves not only protecting workloads and data but also ensuring that roles and responsibilities across DevOps, SecOps, and business units are clearly defined. Gaps in visibility, misconfigurations, and weak credential practices are prompting organizations to rethink how they secure cloud-native environments.
Enterprises are now investing in purpose-built cloud security tools, enforcing stricter access controls, and enhancing real-time monitoring across hybrid and multi-cloud setups. This shift marks a growing recognition that effective cloud security isn’t just a technical safeguard—it’s a foundational element of business resilience and trust.
Why Cybersecurity is Essential for Modern Organizations
As digital transformation accelerates, businesses rely more than ever on connected systems and digital data. Without strong cybersecurity measures, this shift leaves organizations exposed to various vulnerabilities, and operational disruption. Therefore, implementing effective cybersecurity practices is a business imperative. Here’s how cybersecurity plays a vital role in protecting today’s digital-first enterprises.
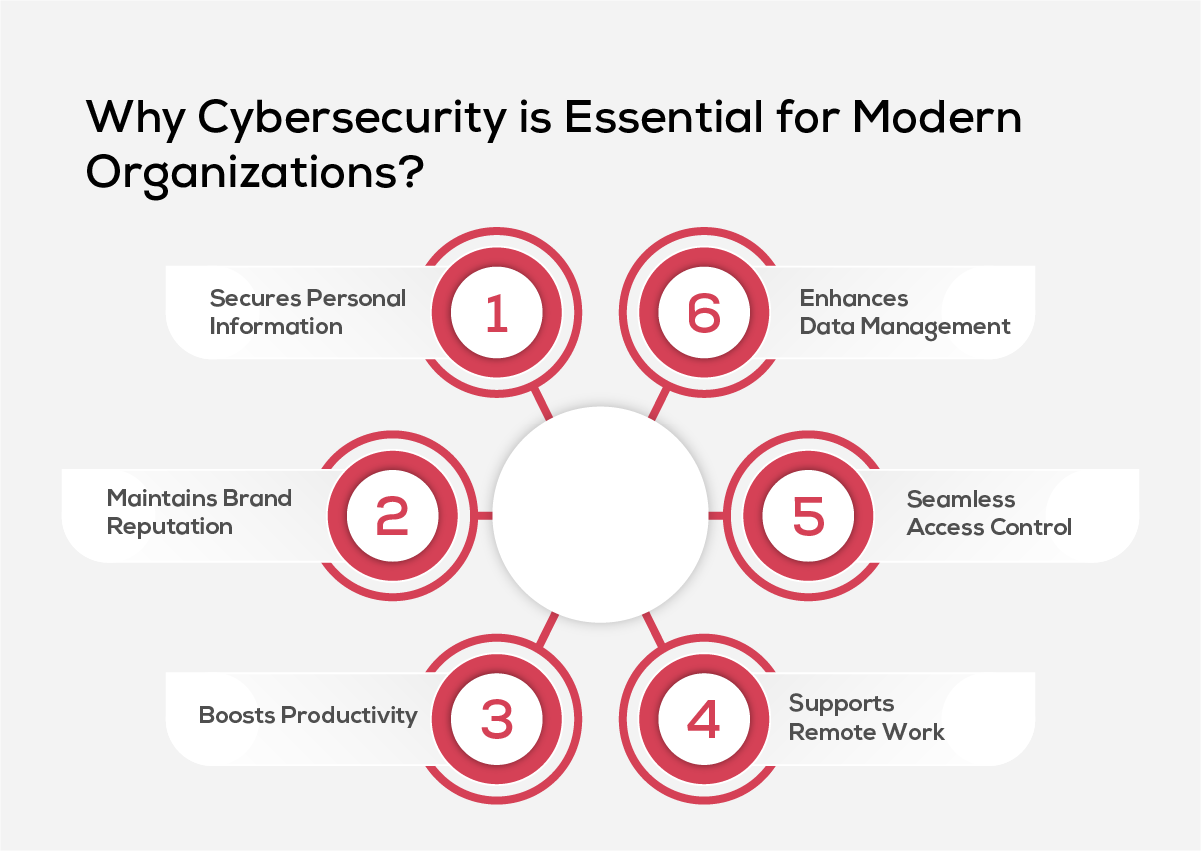
1. Secures Personal Information
Cybersecurity safeguards personal and organizational data from unauthorized access or misuse—especially from within the organization. It helps prevent data leaks that may arise from former employees, third-party vendors, or trusted partners by enforcing strict access controls, monitoring user activity, and detecting suspicious behavior. This protection is essential to maintaining both individual privacy and the organization’s overall security posture.
2. Maintains Brand Reputation
Trust is a key part of any brand. When customer data is protected through strong security frameworks, businesses reduce the risk of reputational fallout. It also demonstrates compliance with industry standards, showcasing the organization's commitment to responsible data handling. This proactive approach to protection reinforces brand credibility and positions the business as a trusted partner in the eyes of customers, partners, and stakeholders.
3. Boosts Productivity
Secure systems help reduce downtime and keep productivity on track by preventing disruptions caused by malware and viruses. Investing in advanced security solutions like regular virus scanning and improved firewalls and backups, ensure smoother operations. Additionally, educating the employees about suspicious links, scams, and unsafe practices plays a vital role in preventing breaches and maintaining overall productivity.
4. Supports Remote Work
A strong cybersecurity foundation allows organizations to embrace remote work with confidence. By securing endpoints, networks, and cloud environments, businesses can ensure safe access to systems from any location. Robust security measures also help maintain data privacy, reduce exposure to risks, and enable remote teams to collaborate without disruption. As work-from-anywhere models become the norm, cybersecurity plays a key role in sustaining flexibility and productivity at scale.
5. Seamless Access Control
Centralized access control helps streamline user permissions across systems and applications. It reduces the risk of unauthorized access and protects sensitive data. Role-based access makes it easier to manage users and maintain compliance. This approach strengthens security without complicating day-to-day operations.
6. Enhances Data Management
Effective cybersecurity plays a critical role in strengthening data management practices. By protecting data from unauthorized access, tampering, or loss, organizations can ensure accuracy, integrity, and availability across systems. This not only helps maintain customer trust and business continuity but also supports compliance with data regulations—making security a foundational element of responsible data handling.
Cybersecurity Tools
Utilizing the right cybersecurity help you detect, respond and protect your data. With the availability of these cybersecurity tools, one can ensure that the organisation is safe from cyber-attacks.
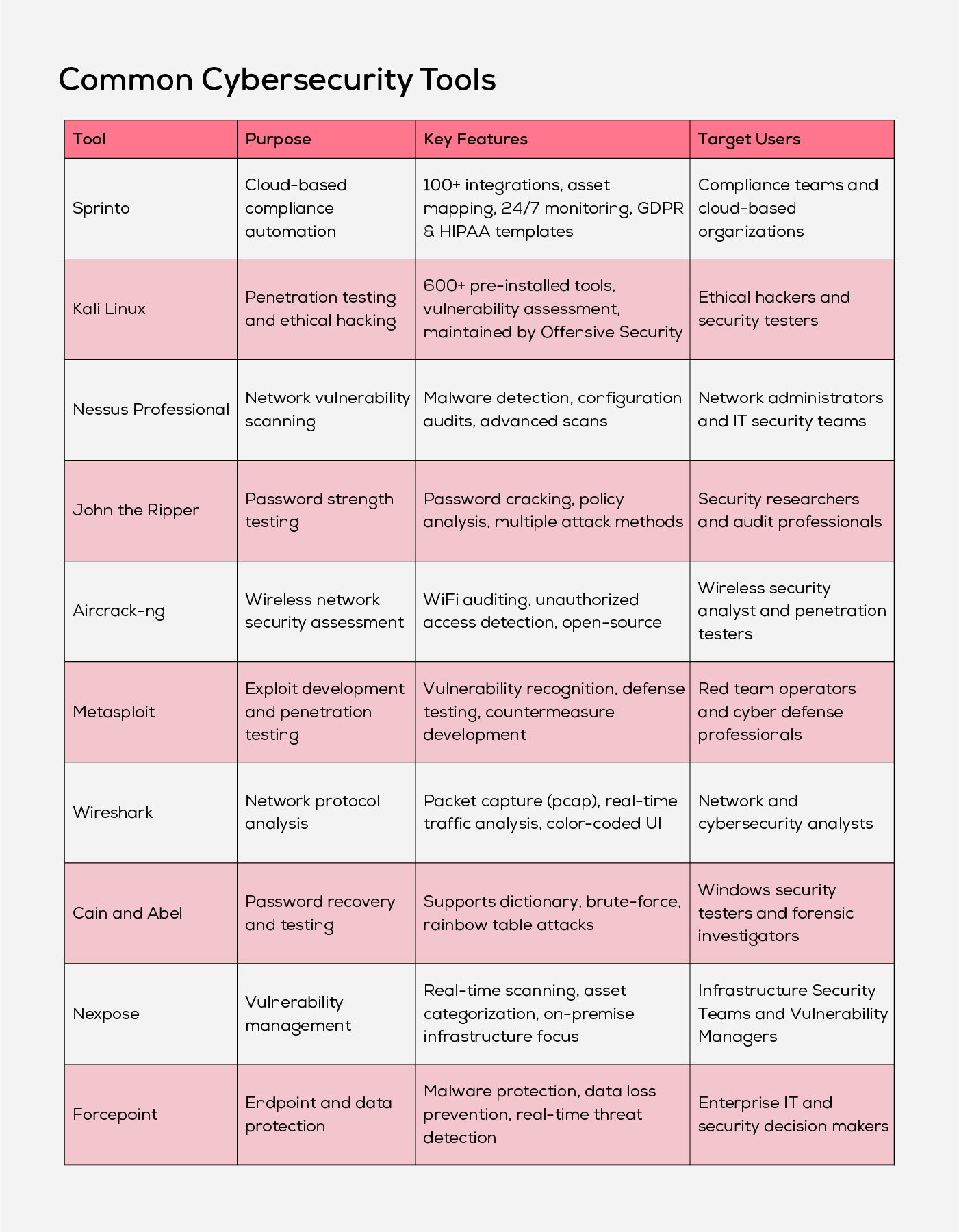
Selecting the right cybersecurity tools early can give organizations a strong foundation to build secure and efficient operations. When tools are well-matched to an organization’s infrastructure, they enhance integration, reduce risk, and streamline workflows. Easy-to-use solutions empower teams to respond faster and more confidently. Tools that adapt to fast development cycles help maintain consistent security without slowing down innovation. By replacing outdated systems with the right set of modern tools, organizations can stay agile, protected, and ready to meet evolving business needs.
Recent Cyberattacks
The recent cyberattacks have highlighted the need for businesses to stay proactive in the cybersecurity field. Here are some of the major giants that fell prey to the cybercriminals.
-
CrowdStrike-Microsoft Outage
A global IT outage occurred in July 2024 after a faulty update from CrowdStrike’s Falcon Sensor caused widespread crashes across Windows systems. The issue affected over 8 million devices and disrupted critical operations in sectors like aviation, banking, and healthcare. Though not a cyberattack, the incident exposed the cascading risks of centralized software dependencies and underscored the importance of rigorous update testing and response protocols.
-
Disney's data leak
Hacktivist group Nullbulge, based in Russia, claimed responsibility for a massive data breach at Disney, leaking 1.2 terabytes of sensitive data from internal Slack channels. The stolen dataincluded confidential project information, messages, files and login credentials, reportedly accessed through an insider using stolen cookies. Nullbulge published the stolen data on BreachForums and mirror sites, criticizing Disney's handling of artist contracts and AI usage.
-
Tile Data Breach
Tile, the popular Bluetooth tracking Device Company suffered a data breach that exposed consumer information, including names, addresses and phone numbers. The cybercriminals also accessed internal tools used to process law enforcement location requests. The breach led to a ransom demand made to Tile’s parent company, Life360, highlighting the growing risks tied to connected consumer tech.
-
Ticketmaster Data Breach
A massive data breach hit Ticketmaster, with the hacking group ShinyHunters claiming responsibility for stealing sensitive information from over 500 million customers. Known for targeting personal records for sale on the dark web, this group has been active since 2020 and has previously breached companies like Microsoft and AT&T, affecting 70 million customers in March, 2024.
Conclusion
With the growing complexity of cyber threats and the evolving digital landscape, choosing the right tools and practices is more important than ever. Organizations must prioritize regular software updates, strong authentication measures, continuous employee training and frequent security evaluations to protect sensitive information and create a protected digital environment. This approach is essential for staying one step ahead of cyber threats.
Take the next step in securing your business with our Vulnerability Assessment and Penetration Testing (VAPT) services. Stay informed about the latest high vulnerabilities, data breaches and ransomware trends by subscribing to our monthly cybersecurity newsletter—your go-to source for practical insights and expert updates.
Frequently Asked Questions
1. What are the common types of cybersecurity threats today?
Organizations face multiple cybersecurity threats, including phishing attacks, ransomware and malware attacks. Additionally, DDoS attacks pose significant risks, which makes it crucial for businesses to prioritize cybersecurity and implement effective measures.
2. What are the factors required for selecting the cybersecurity tools?
When selecting cybersecurity tools, it's essential to consider the organization's requirements, including budget limitations and scalability needs. By conducting a vulnerability assessment, one can identify the most effective tools to boost the cybersecurity defences and protect the organization from potential threats.
3. How can businesses protect themselves from threats?
To enhance cybersecurity, organizations should prioritize regular software updates, use strong and unique passwords and implement multi-factor authentication. Additionally, investing in antivirus and anti-malware software can help prevent cyber threats and protect data.