-
 Reduce Down Time
Reduce Down Time  Minimize Breach Impact
Minimize Breach Impact  Quick Response Time
Quick Response Time  Cost Control
Cost Control
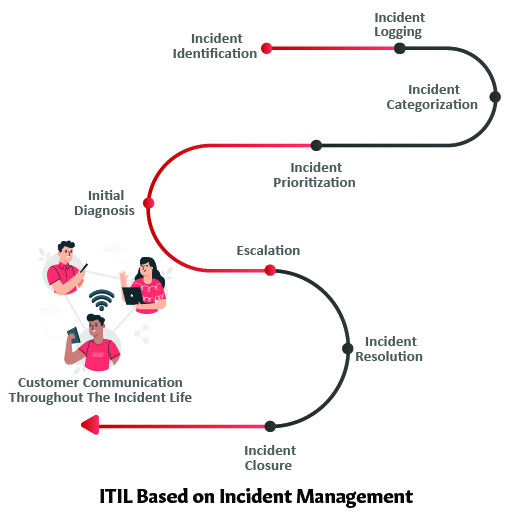
At Inspirisys, our approach to security operations support starts with the identification of customer requirements, implementation, monitoring, tuning, and utilization of appropriate tools. We understand the challenges associated with keeping an organization secure and we leverage our experience in implementing Security Operations Centers for small and large organizations. Inspirisys SOC provides visibility analysis, and action, not only based on logs but also based on network packets. We capture logs, network traffic, and analyze them for abnormalities that point to intrusions. We also offer an incident response with the best in class remediation to thwart attacks. We support enterprises in redefining security operations to cope with evolving cyber threats.
What is a Security Operations Center?
A Security Operations Center operates in many ways that are analogous to the human immune system, which actively monitors, hunts, recognizes, alerts, and prevents/neutralizes real-time cyber-threats. This requires a team of dedicated security analysts with access to the latest threat intelligence and knowledge of the evolving security threat landscape. SOC typically uses event ingestion and analysis tool called SIEM (Security Information and Event Management) that collects a voluminous amount of security events, logs, packets from systems across the enterprise. This allows analysts to correlate events, hunt malicious or suspicious access patterns, and identify threats based on active threat intelligence. Analysts may also handle or suggest remediation such as patch application, configurations modification, and system upgrades.
Why SOC?
As almost all the organizations have started to adopt a remote-working strategy to cope with the pandemic situation, having cybersecurity solutions for remote working conditions is becoming mandatory. A recent cybersecurity report indicates that 31% of enterprises have experienced cyber-attacks on operational technology infrastructure. This also denotes that vulnerabilities are rising in number and broadening severities too. The result to reduce these intrusions leads enterprises to invest in a Security Operations Centre (SOC). The main objective of a SOC is to detect monitor, analyze and react to security incidents with the integration of futuristic tools, cutting-edge technologies, and a robust security strategy.

We defend your organization from Cyber Threats with
- High-Speed Threat Detection
- Immediate Intrusion Alerts
- Quick Incident Response
- Real-Time Threat Intelligence
- Proactive Threat Hunting
- 24*7*365 operations
- Smart IT Ticketing System
- Dedicated Security Experts
- Trusted World-class Strategic Partnerships
 Log Management
Log Management
Our centralized & fully integrated global SOC is seamless for storing raw logs from multiple sources. It enables common compliance & regulatory requirements. Logs provide real-time & historical views of collected information, enabling forensic investigations.
 Correlation & Threat Intelligence
Correlation & Threat Intelligence
We offer SIEM correlation engines and rules that are fine-tuned to each customer for continuous detection of critical alerts & incidents. Events from multiple sources are aggregated to identify suspicious or anomalous patterns that may represent a threat.
 Security Monitoring & Incident Response
Security Monitoring & Incident Response
Log monitoring for early detection of threats, to meet regulatory compliance & for deep-dive investigations. We deeply investigate & triage potential security incidents. An identified security incident is communicated to customers along with relevant details.
 Advanced Threat Analytics with AI
Advanced Threat Analytics with AI
Our SOC in IT security is powered by a big-data analytics platform that uses feeds from multiple sources, combined with techniques of Machine Learning and AI. We use Hadoop, Storm, and Spark with both streaming and map-reduce analytics.
 Malware Analysis
Malware Analysis
Automated malware analysis processor analyses certain types of file objects to assess the malicious nature of a file. Some of the techniques include Network Session Analysis, Static File Analysis, Dynamic File Analysis & Security Community Analysis.
 User and Entity Behaviour Analysis (UEBA)
User and Entity Behaviour Analysis (UEBA)
UEBA uses ML and statistical analysis to create a baseline of normal patterns & detect anomalous behaviour. It is based on creating Standard profiles & behaviours of both users and entities. It helps in better detection of insider threats & targeted attacks.
 Orchestrator (SOAR)
Orchestrator (SOAR)
Orchestrator provides automation of security operations, threat & vulnerability management, and incident response. It enables your organization with quicker resolution and operational efficiency driven by playbooks for automated detection and response.
 Dedicated Customer Dashboard & Reports
Dedicated Customer Dashboard & Reports
With SOC as a service we offer dedicated dashboards and on-demand report generation service for customers are provided to monitor performance, identify trends and speed up decisions. Customer-specific reports can be added on request.
 Problem Management
Problem Management
We provide personalized consulting services to evaluate security posture for organizations. In addition to identifying the root cause of incidents, steps are also suggested to prevent the recurrence of such incidents and minimize future impact.
 Penetration Testing as a Service
Penetration Testing as a Service
Our application & network security experts probe and penetrate the security and defences of your application & systems. These activities can be detected and reported thereby quickly identifying weak spots where improvements are required.
 Vulnerability Assessment as a Service
Vulnerability Assessment as a Service
Our vulnerability assessment experts identify, classify and prioritize the vulnerabilities. Remediation and mitigation steps are applied for specific business-critical vulnerabilities. With Vulnerability Assessment we help to protect your data and network.
 Network Forensics as a Service
Network Forensics as a Service
Our Network Forensics as a Service captures and stores packets from the entire organizational network. With a team of network forensics analysts, we completely analyse the recorded packets and log to detect and reconstruct intrusions.
Seamless Compliance with Information Security Standards
- PCI
- ISO 27002
- HIPAA
- SOX
- BASEL II
- BILL 198
- FERPA
- FFIEC
- FISMA
- GLBA
- GPG13
- NERC CIP
- NISPOM
- SSAE 16
Why Choose Inspirisys?
02
Expertise
With nearly 3 decades of expertise, we empower enterprises defensive cyber security solutions with state-of-the-art technologies to tide over the increasing cyber threats.
04
Combat Modern Security Threats
We develop an effective cyber security strategy based on the current security posture of an organization to combat today’s cyber threats.
06
Remote-Ready
Our remote work solutions with modern VPN technology helps organizations to secure the remote work-force and to keep cyber criminals at the bay.
01
NIST Framework
We follow NIST Framework that provides a cost-effective way for organizations to line their cyber security strategies and bolster the security posture around cyber risk and compliance.
03
Preventive & Progressive Approach
Our preventive and progressive approach help organizations to take the lead while addressing these threats,focus on the needs of your business, while we assist you with building customer trust.
05
Compliance
With deep expertise in the cyber security landscape, we improve your compliance with the national and international information security standards.
01
NIST Framework
We follow NIST Framework that provides a cost-effective way for organizations to line their cyber security strategies and bolster the security posture around cyber risk and compliance.
02
Expertise
With nearly 3 decades of expertise, we empower enterprises defensive cyber security solutions with state-of-the-art technologies to tide over the increasing cyber threats.
03
Preventive & Progressive Approach
Our preventive and progressive approach help organizations to take the lead while addressing these threats, focus on the needs of your business, while we assist you with building customer trust.
04
Combat Modern Security Threats
We develop an effective cyber security strategy based on the current security posture of an organization to combat today’s cyber threats.
05
Compliance
With deep expertise in the cyber security landscape, we improve your compliance with the national and international information security standards.
06
Remote-Ready
Our remote work solutions with modern VPN technology helps organizations to secure the remote work-force and to keep cyber criminals at the bay.