Quick Summary: VAPT tools are crucial for identifying vulnerabilities and improving security. With various options available, choosing the right tool is crucial for organizations aiming to protect their assets. We’ll explore the key VAPT tools, their features, and features, helping you select the best solution to strengthen your security posture.
In today's fast-evolving digital world, cybersecurity has become imperative for organizations. As reliance on digital platforms, cloud services, and interconnected networks increases, so does the risk of sophisticated cyber threats. Safeguarding sensitive data and maintaining system integrity requires more than just reactive measures; it demands proactive strategies that can identify and address vulnerabilities before they can be exploited.
The 2017 Equifax breach serves as a stark reminder of the consequences of insufficient security measures. A vulnerability in the company’s web application framework exposed the personal and financial data of 147 million customers. Despite conducting routine security scans, Equifax failed to identify the exploited weakness, highlighting the need for thorough penetration testing to detect vulnerabilities early.
This is where Vulnerability Assessment and Penetration Testing (VAPT) tools come into play. These tools identify weaknesses in your security and simulate real-world attacks, providing valuable insights to help you address vulnerabilities before they lead to breaches.
In this blog, we’ll explore the top 10 VAPT tools, highlighting their key core capabilities to help you make informed decisions about strengthening your cybersecurity posture. To fully understand their value, let’s first examine what VAPT is and how it fits into an effective security strategy.
What is VAPT?
Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive security evaluation process that identifies, assesses, and addresses vulnerabilities in an organization’s systems, networks, and applications. This dual approach combines Vulnerability Assessment, which systematically scans for potential weaknesses, with Penetration Testing, which simulates real-world attacks to test the effectiveness of security measures. By adopting VAPT, organizations can protect against threats, ensure data confidentiality, and significantly reduce the risk of breaches. Additionally, VAPT helps organizations stay ahead of industry trends and maintain compliance with evolving security standards.
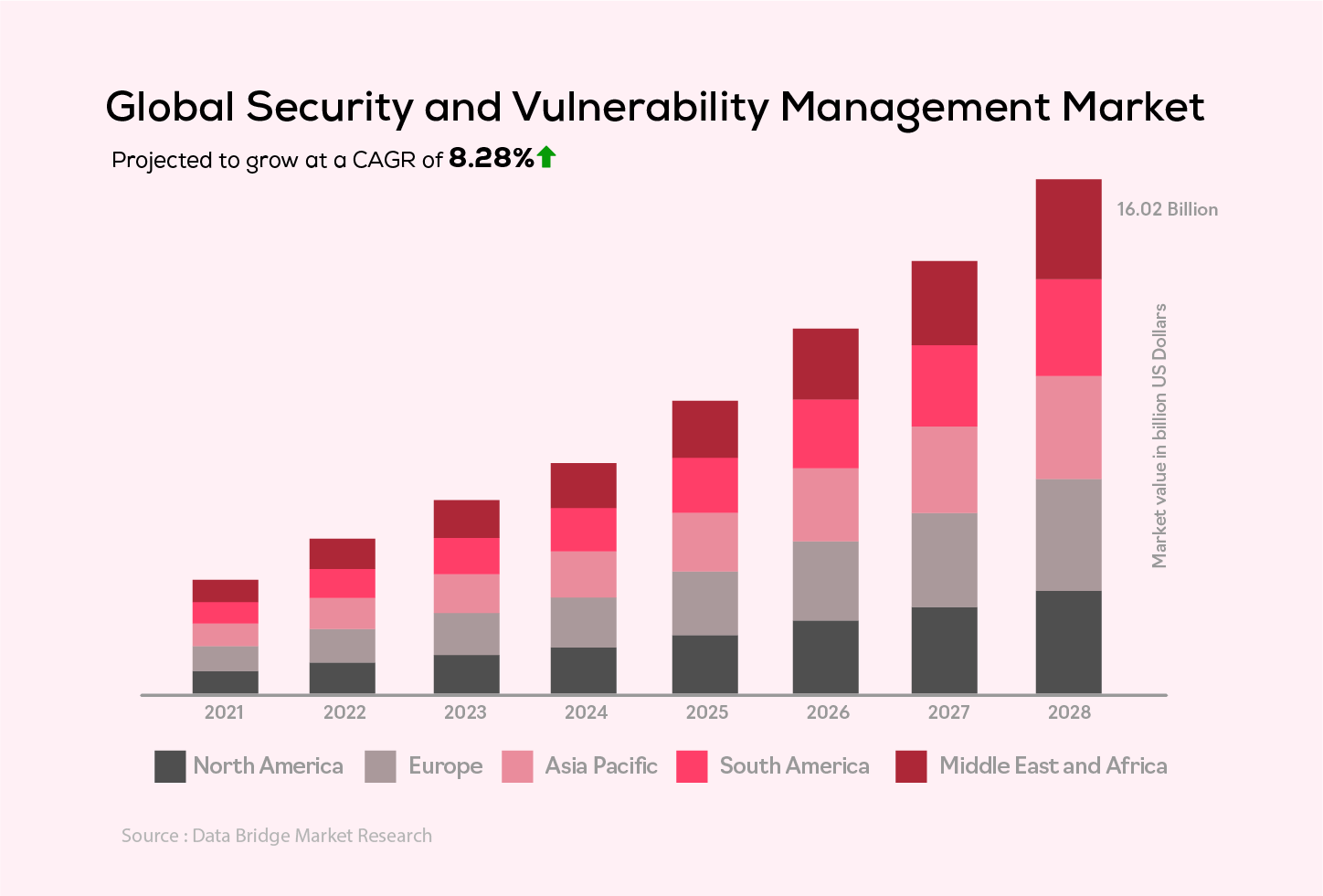
The importance of such proactive measures cannot be overstated in today’s threat landscape. In November 2023 alone, 470 publicly reported breaches affected 519 million records, bringing the total number of compromised records to nearly 6 billion this year. These alarming statistics highlight the urgent need for organizations to act swiftly in reducing breach risks and safeguarding sensitive data from cyber threats.
According to Data Bridge Market Research, the security and vulnerability management market is projected to reach USD 16.02 billion by 2028, growing at a CAGR of 8.28%. As cyber threats evolve, the demand for robust security solutions like VAPT continues to rise.
Importance of VAPT for Organizations
In today’s digital era, the rise in sophisticated cyber-attacks and data breaches places immense pressure on organizations to safeguard sensitive information. At the same time, consumers are increasingly cautious about sharing personal data, expecting you to uphold high security standards. To meet these expectations and mitigate risks, it’s essential that you proactively identify and address vulnerabilities in your systems. VAPT plays a critical role in fortifying your defences and ensuring data security. Let’s explore why VAPT is indispensable in today’s evolving threat landscape:
1. Lower Cyber Threats
VAPT takes a proactive approach to cybersecurity, addressing potential threats before they arise. By regularly assessing vulnerabilities and conducting tests, VAPT helps you stay one step ahead of cybercriminals, reducing the risk of successful attacks and minimizing potential damage.
2. Security Management
Incorporating VAPT into your company’s cybersecurity plan enables you to adopt a proactive approach in preventing cyberattacks. By identifying vulnerabilities before they can be exploited, you can avoid the financial and reputational consequences of cyberattacks, including data breaches, system downtime, and financial losses. This strategy not only helps prevent data breaches but also saves money in the long run. Additionally, it ensures that your business stays ahead of emerging threats and secures a more resilient future.
3. Avoiding the Financial Losses
The financial consequences of a cyberattack can have a devastating and long-lasting impact. Beyond direct financial losses, maintaining customer trust is equally critical. A cyberattack can lead to significant costs, including system restoration, legal fines for failing to protect sensitive information and the loss of customer confidence and trust.
4. Smart Decision-Making
VAPT reports are essential decision-making tools, providing more than just technical data. They help create a clear improvement plan, enabling you to make informed decisions that strengthen your overall security system. The insights serve as a roadmap, guiding your business through the cybersecurity landscape. By leveraging this information, you can make strategic security investments, ensuring robust and effective security measures.
Top Vulnerability Assessment and Penetration Testing Tools
As cyber threats continue to evolve, leveraging the right VAPT tools becomes essential for organizations looking to stay ahead of potential vulnerabilities. These tools not only identify and report weaknesses but also play a critical role in strengthening your organization’s overall digital security. With the right VAPT tools in place, you can ensure that your systems are robust and protected against emerging threats.
When it comes to safeguarding your digital assets, choosing the right tools is crucial. Here are our top picks for the best Vulnerability Assessment and Penetration Testing tools:
Web Application Penetration Testing Tools
Web application penetration testing is a critical measure that simulates real-world attacks to identify and fix vulnerabilities in web applications. By leveraging a combination of automated tools and manual techniques, security professionals can test web applications for weaknesses that hackers might exploit. This helps prevent data breaches, stealing sensitive data or other malicious activities that could compromise the integrity of the app. Let’s take a look at the leading web application penetration testing tools that can strengthen your organization’s security measures.
- Securelayer7
As a leading provider of continuous web application penetration testing, Securelayer7 brings together the strengths of automated and manual testing. This approach enables the identification of known Common Vulnerabilities and Exposures (CVEs) in application libraries, providing a comprehensive solution for safeguarding web applications against potential security threats. It empowers customers to identify and address security gaps including issues with authentication, logic vulnerabilities and logic flow.
Key Features:
- Performs patch verification to address compliance issues.
- Generates detailed reports, including an executive summary, test scope, approach and summary of OWASP Top 10 vulnerabilities.
- Features a user-friendly interface that simplifies the process of conducting assessments and interpreting results.
- Metasploit
Metasploit is a powerful web application penetration testing tool, designed to simulate real attacks on web applications, identify network and server vulnerabilities and highlight weak points that require immediate attention to prevent security breaches. One of its distinctive features is its ability to conduct manual and automated testing in parallel, significantly reducing the overall testing time and effort required. Once scanning is complete, Metasploit delivers a detailed report that identifies vulnerabilities and provides a remediation plan, allowing businesses to address vulnerabilities and enhance overall security effectively.
Key Features:
- Easy to use and customizable.
- Runs on macOS, Windows and Linux.
- Preferred for executing large network penetration tests.
- Wireshark
Imagine being able to thoroughly test web applications with a tool that can examine the intricacies of hundreds of different protocols. Wireshark supports a wide range of protocols, including IPsec, WEP, SNMPv3 and ISAKMP and enables users to inspect and identify security vulnerabilities. It also provides live tracking for various technologies, including ATM, Bluetooth, USB, Ethernet and FDDI.
Key Features:
- Effectively monitors web application network traffic and identifies threats faster.
- Helps troubleshoot network performance issues.
- Available for free.
Mobile Application Penetration Testing Tools
The widespread adoption of mobile apps has significantly expanded the potential attack surface for cybercriminals. Mobile app pen-testing tools are essential for identifying and addressing security weaknesses, thereby protecting sensitive user data and protect brand reputation. Now, let’s explore some of the top tools that can help organizations enhance their mobile app security:
- Kali Linux NetHunter
Kali Linux NetHunter is an open-source penetration testing platform built on an Android-based operating system. Widely regarded as one of the top mobile app penetration testing tools, it allows security professionals to conduct real-world attacks and uncover vulnerabilities in mobile apps and devices. Leveraging the power of Kali Linux, NetHunter transforms compatible Android devices into portable penetration testing instruments, enabling comprehensive mobile app security assessments, vulnerability detection, and remediation.
Key Features:
- When paired with compatible hardware, NetHunter's WiFi injection capabilities allow security teams to launch targeted attacks on wireless networks, helping to identify vulnerabilities before malicious actors can exploit them.
- Adaptable and scalable, making it suitable for various mobile penetration testing scenarios.
- The toolkit is a versatile collection of tools that cater to various stages of the penetration testing process, including data collection, vulnerability identification, exploitation and post-exploitation, allowing security teams to conduct comprehensive security assessments.
- Mobile Security Framework (MobSF)
MobSF or Mobile Security Framework, is a leading mobile app penetration testing tool designed to address the unique security challenges of mobile applications. Supporting both Android and iOS platforms, MobSF offers comprehensive features, including static, dynamic, and malware analysis to deliver thorough security assessments.
Key Features:
- MobSF integrates with DevSecOps and CI/CD pipelines through REST APIs and CLI tools, streamlining the security workflow.
- Its static analysis feature allows users to upload mobile app binaries and receive detailed security reports, making it accessible to individuals without security knowledge.
- Its dynamic analysis environment offers an interactive experience for experienced mobile security researchers, enabling them to explore mobile app security in detail and discover hidden vulnerabilities.
- Data Theorem
Data Theorem is a security solution designed to protect applications, with a focus on mobile app security. It identifies and resolves critical security risks across your application environment. The platform conducts thorough app analysis and continuous monitoring using a combination of static, dynamic and runtime techniques to evaluate every app binary build. It also automatically reviews apps for blockers in the Apple App Store and Google Play, sending alerts via Slack, Teams and emails for high-risk issues.
Key Features:
- The platform’s one-click reporting feature generates a report with a single click, saving time and effort.
- Through the integration with CI/CD tools, the platform delivers DevSecOps solutions.
- The platform enables collaboration among teams by supporting customizable user access roles, ensuring that managers, security teams and developers can work together efficiently.
API Security Testing Tools
APIs are the backbone of modern software interactions, enabling seamless communication and data exchange across applications. However, their critical role makes them prime targets for cyberattacks. API security testing tools are essential to uncover vulnerabilities, prevent data breaches, and ensure the reliability of these interfaces. By identifying bugs, undefined behaviours, and security gaps, these tools help protect sensitive data and maintain your organization’s reputation.
Explore our top picks for API security testing tools that can enhance your API protection strategy:
- 42Crunch
42Crunch’s API Security Testing Tool helps you identify vulnerabilities and provides clear guidance on remediation. The platform's API Security Audit tool performs a detailed static analysis of the OpenAPI definition file, uncovering security risks and offering actionable recommendations. By thoroughly examining the OpenAPI contract, it detects issues such as data leakage, weak authentication mechanisms, and injection flaws, delivering a comprehensive report to guide your security efforts.
Key Features:
- Seamlessly integrates with various CI/CD platforms, allowing developers to incorporate security into their workflow.
- Conducts over 300 security checks, offering live endpoint testing, actionable reports and immediate security scoring.
- Provides a streamlined security workflow, combining static analysis with live endpoint testing for end-to-end API security.
- Beagle Security
This AI-powered pen-testing tool identifies security vulnerabilities in web applications and APIs, providing actionable insights to help you address them quickly and effectively. It extends its testing capabilities to REST APIs and GraphQL endpoints, efficiently detecting weaknesses. Additionally, it integrates with CI/CD pipelines, enabling you to identify and resolve security weaknesses in pre-production environments.
Key Features:
- Scans over 3000 vulnerabilities, including OWASP Top 10 and CWE Top 25 standards.
- Mimics human-like penetration testing, using advanced logic to select relevant test cases, eliminate false positives and deliver precise detection.
- Enables users to schedule automated security checks, integrate with popular platforms and implement role-based authorizations.
Cloud Penetration Testing Tool
As businesses increasingly adopt cloud services, securing these environments becomes critical. Cloud penetration testing integrates vulnerability scanning with simulated attacks to uncover potential security gaps. This approach helps you strengthen your cloud infrastructure, protect sensitive data, and maintain compliance with industry standards.
Here are some of the top cloud penetration testing tools to enhance your cloud security:
- Astra Pentest
Astra Pentest takes a proactive approach to cloud security, conducting over 9,300 tests to uncover hidden weaknesses and provide actionable insights to fortify your defences and prevent potential breaches. It is compatible with AWS, Azure and GCP, ensuring zero false positive assurance.
Key Features:
- User-friendly and has an easy-to-navigate interface.
- CI/CD pipeline integration to automate security testing and transition from DevOps to DevSecOps.
- Comprehensive vulnerability scanner with the ability to re-scan, allowing you to validate remediation efforts and maintain a secure posture.
- Intruder
Intruder, a cloud-based vulnerability scanner that identifies and prioritizes errors in online systems, enabling you to strengthen defences and protect against threats. Its advanced scanning capabilities keep you ahead of emerging risks, saving time and effort in managing vulnerabilities. The tool checks for missing patches, configuration issues, and web application vulnerabilities such as cross-site scripting and SQL injection.
Key Features:
- Prioritizes high-severity vulnerabilities, regularly scanning for new weaknesses that may be targeted by attackers.
- Detects critical security flaws early, enabling proactive threat mitigation.
- Provides evidence-based, actionable insights to help you effectively address vulnerabilities.
- Nessus
Nessus is a powerful cloud-based tool that helps you discover security weaknesses and enhance your protection. It simplifies vulnerability assessment, enabling you to rapidly identify and remediate security threats. By streamlining vulnerability discovery, Nessus allows you to focus on securing your IT infrastructure and protecting against threats.
Key Features:
- Provides real-time alerts when a vulnerability is detected
- Scans systems, apps and configurations for flaws
- Offers a wide range of vulnerability tests
Key Features to Consider When Choosing the Right VAPT Tool
Now that you’ve explored some of the top VAPT tools, it’s important to know what to look for when evaluating the best fit for your organization. While each tool offers unique capabilities, certain key features are essential for ensuring effective vulnerability scanning and penetration testing. Let’s dive deeper into the factors that should guide your choice of the right VAPT tool for your security needs.
1. Accuracy
A vulnerability scanning tool should accurately detect a range of vulnerabilities, minimizing false positives and negatives. This allows security teams to prioritize and address threats promptly. An ideal tool offers a clear view of vulnerabilities, ensuring that the most critical threats are tackled without distraction.
2. False Positive Minimization
A high-quality VAPT tool reduces false positives to ensure that the security team isn’t overwhelmed with non-critical issues, allowing them to focus on actual risks.
3. Scanning
Vulnerability assessment tools are built around their scanning capabilities, conducting comprehensive scans to detect potential vulnerabilities across all connected devices, applications and systems.
This scanning process is continuous and regular, essential for protecting your systems as new vulnerabilities emerge. Advanced tools provide real-time scanning for continuous visibility and enable immediate threat responses.
4. Scalability
The tool should be scalable to accommodate the growing needs of your organization, whether expanding to new environments, increasing the volume of scans, or supporting additional users.
5. Compliance Support
Ensure the tool helps you meet compliance requirements (e.g., GDPR, HIPAA, PCI DSS) by checking for vulnerabilities relevant to industry standards and regulations.
Common Challenges in Implementing Vulnerability Scanning Tools
While vulnerability scanning tools can significantly enhance your organization’s security, there are several challenges that may arise during implementation. By recognizing and addressing these challenges, you can improve your overall security. Below are some of the common obstacles you may encounter:
1. False Positives
One of the main challenges you may face with vulnerability scanning tools is false positives, where the tool incorrectly identifies non-existent threats. This can lead to wasted time and resources as your team spends effort investigating issues that aren’t actually threats. False positives can hinder the ability to quickly identify and address real security concerns.
2. Privacy Concerns
When using vulnerability scanning tools, you must be mindful of their impact on sensitive data. It's crucial to ensure that the tools are configured to comply with privacy regulations, protecting digital assets from unauthorized access. Proper configuration of scans helps safeguard sensitive data, reducing the risk of exposure during testing.
3. Regular Updates
As cyber threats evolve, it’s crucial for you to regularly update your vulnerability scanning tools to keep them effective in detecting new threats. In larger organizations, tracking these updates can be challenging, and missing them could lead to security gaps and vulnerabilities.
4. Resource Requirements
Running full vulnerability scans can put a strain on your system’s resources, potentially causing slowdowns and disrupting normal operations. To avoid performance issues, you must ensure that your infrastructure can support these tools without impacting your day-to-day activities.
5. System Integration
When choosing vulnerability testing tools, it’s crucial to ensure they integrate smoothly with your existing systems and workflows. This integration is key to maintaining strong defences. Be prepared to allocate time and resources to configure the tools efficiently and integrate them seamlessly into your operations.
Final Thoughts
As technology advances, so do vulnerabilities, putting your organization at greater risk. To stay ahead, regular Vulnerability Assessment and Penetration Testing (VAPT) tools are essential to securing your business and protecting sensitive data.
Choosing the right vulnerability assessment tool can feel overwhelming, given the many options available. Each tool has its unique advantages in identifying and addressing risks. But the key is finding the one that fits your organization’s specific needs.
If you’re struggling to find the ideal VAPT solution for your organization, Inspirisys is here to help. Our tailored VAPT services—including Application VAPT, Endpoint VAPT, Network VAPT, and IoT VAPT—are designed to meet your needs. Let our experts guide you to the best solutions to fortify your security. Don’t wait for a breach to happen—contact us today and take the first step toward better security!
Frequently Asked Questions
1. Why do you require VAPT Tools?
VAPT tools play a crucial role in addressing security weaknesses within system and applications, helping to protect them from security breaches. These tools focus on the most critical vulnerabilities and improve overall security.
2. What are some of the common factors that cause vulnerabilities?
Human errors, complex software, weak password management and loopholes in the system and design.
3. Which VAPT tool is best for small businesses?
For small businesses with limited budgets and resources, Nessus and Intruder are the best choices for vulnerability testing.
4. How to choose the right VAPT tool for the organization?
When selecting a vulnerability testing tool, it's essential to consider factors such as the organization's security requirements, the types of systems that need to be tested, the available budget and the level of technical expertise required.
5. How often should VAPT tools be used?
To maintain optimal security, it’s important to conduct regular assessments. A typical approach is to run vulnerability scans quarterly and perform penetration tests annually.







