Verizon data breach investigation report 2016 states that 40% of all data breaches in the world involved web application attacks.
A fully functioning traditional firewall can’t withstand many of the advanced cyber-attacks. Because it does very little to protect a multi-tier web application. A perimeter firewall opens common ports such as port 80 and 443 to access and interact with hosted sites. Hackers use the same ports to sneak into applications. So a traditional firewall cannot stop an SQL injection or DDOS attack. An application security system must be able to do more than opening and closing the ports.
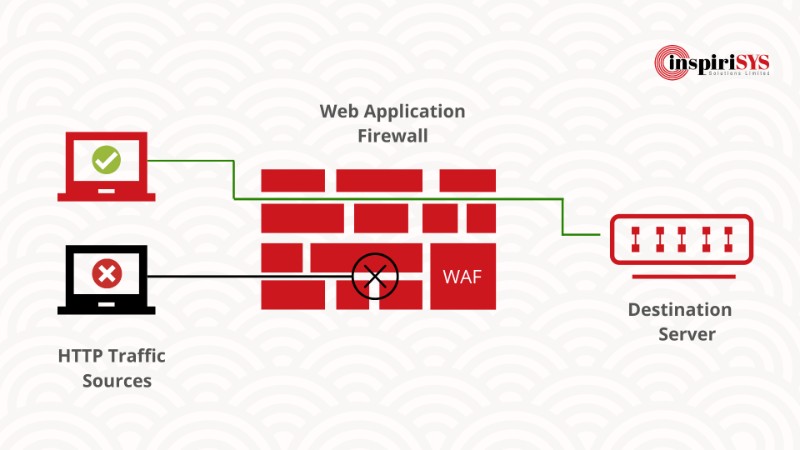
Web Application Firewall (WAF) is an advanced version of a traditional firewall that resides on the outer edge of the network, in front of the public side of a web application. It detects suspicious network traffic and automatically filters the same. It works based on specific security rule sets. People misconceive that Intrusion Protection Systems extensively support firewalls. But, they can only monitor the incoming network traffic but not equipped to interpret the complex nature of HTTP traffic. WAF intercepts & analyzes each and every HTTP request before they reach the web application. It protects web applications from the below threatening cyber-attacks.
Zero-day exploits
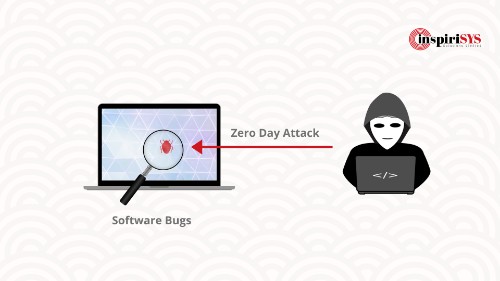
Bug fixing is a never-ending process in application development and maintenance. Bugs are flaws in an application that leaves it vulnerable. Most of the organizations come to know about the existence of vulnerability only when an attack happens. Even more pathetic situation is, they don’t have any quick fixes or patches. In February 2017, the first Equifax breach happened due to a vulnerability in apache struts. Apache released a patch in March 2017. Equifax’s systems remained unpatched for months. Attackers used this time to mount a sophisticated multi-layered breach. It remained hidden until Equifax noticed suspicious activities. They took action to lock down the web application. But it was too late. Millions of confidential records were stolen.
The temporary patching ability of WAF is a savior in these kinds of situations. It is equipped with machine learning capabilities and blocks bad request by analysing attack patterns. It virtually patches the web application with known vulnerabilities and updates the WAF profile when the developer officially patches the application.
SSL camouflage
Much of today’s web traffic is encrypted to protect data from man-in-the-middle attacks. But hackers are taking advantage of this by using “HTTPS” as a camouflage to avoid detection. On March 15, 2011, the Registration Authority (RA) of Comodo was compromised. Attackers stole the username and password of a Comodo Trusted Partner in Southern Europe. Consequently breaching the Registration Authority, about nine digital certificates across seven different domains including Yahoo, Google, Skype, and Mozilla were fraudulently taken over by the attackers.
Since WAF stands between the public and web applications, it decouples traffic between the web server and the internet. It terminates the encrypted connection, analyze the traffic and forward it to the web application in HTTP. In other words, it is working as an inbound or reverse proxy. The response traffic is sent back to WAF where it is encrypted and forwarded to the user using the HTTPS protocol.
Parameter Tampering
Customers interact with web apps and provide information or sending communication to the web app owner. Some of the parameters helping to exchange information are cookies, hidden forms, strings of code and URL tracking snippets. Hackers look for vulnerabilities within these parameters to extract useful information and perform identity theft.
WAF blocks all parameter discrepancies by analyzing user behaviour when they interact with parameters and codes. It recognizes automated tools that are executing parameter tampering commands.
Cross-site Scripting (XSS)
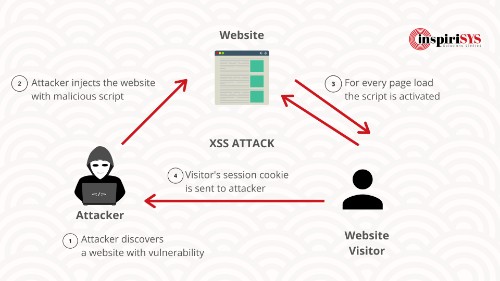
XSS is similar to SQL injection. Attackers attach harmful codes into a legitimate website and it is automatically executed when the victim loads the website. These codes can be attached at the end of a URL or it can be posted directly onto a page. In 2014, eBay suffered a huge XSS attack. The hackers exploited a common vulnerability to inject malicious JavaScript into several listings for cheap iPhones. When a user clicked on these links they were taken to another site disguised to be eBay log-in page. On further investigation, it was revealed that the page was hosted elsewhere and had been designed to harvest user log-ins for the hackers.
WAF enforces security rules to prevent reflected cross-site scripting. Its real-time monitoring scans URLs, query strings, headers and HTML body for vulnerable scripts. When it detects suspicious scripts, it blocks and report or delete the script based on the security rules.
ISL WAF SERVICES
With a proven track record of providing application security solutions, we have built strong customer trust and support. Our Web Application Firewall implementation protects your organization from zero-day exploits, SSL camouflage, parameter tampering, XSS attacks, and other dangerous cyber-threats. We safeguard your confidential and sensitive data from slipping into the wrong hands. With an up-to-date WAF profile, we ensure 24*7 security to your web application. Click here to talk to our WAF security expert to protect your web application now!