Protecting your organization and your customers’ data is the need of the hour as cyber threats are invading sensitive data like never before. Firewall penetration testing plays a major role in defending today’s organizations. Any company concerned about its security posture builds the first line of defense with a firewall, not only to monitor the incoming and outgoing traffic of the network but also to block suspicious traffic as specified in the security protocol. When the firewall was popularized it could only block well-known threats. However, it has adapted to modern times and examines the packets entering into the network, learns the pattern, and determines the trustworthiness. However, some Advanced Persistent Threats (APTs) can lurk into the network, disguised as normal to bypass the capabilities of the firewall. Fortunately, Firewall Penetration Testing can exploit the vulnerabilities that could compromise a network.
This blog covers:
Know your Firewall Variant before Testing
Firewall penetration testing is performed in multiple stages to maintain the most comprehensive delivery. It includes analysing the rule-based configuration, firewall configuration, and identifying the vulnerabilities. Different types of firewalls require different methodologies of penetration testing.
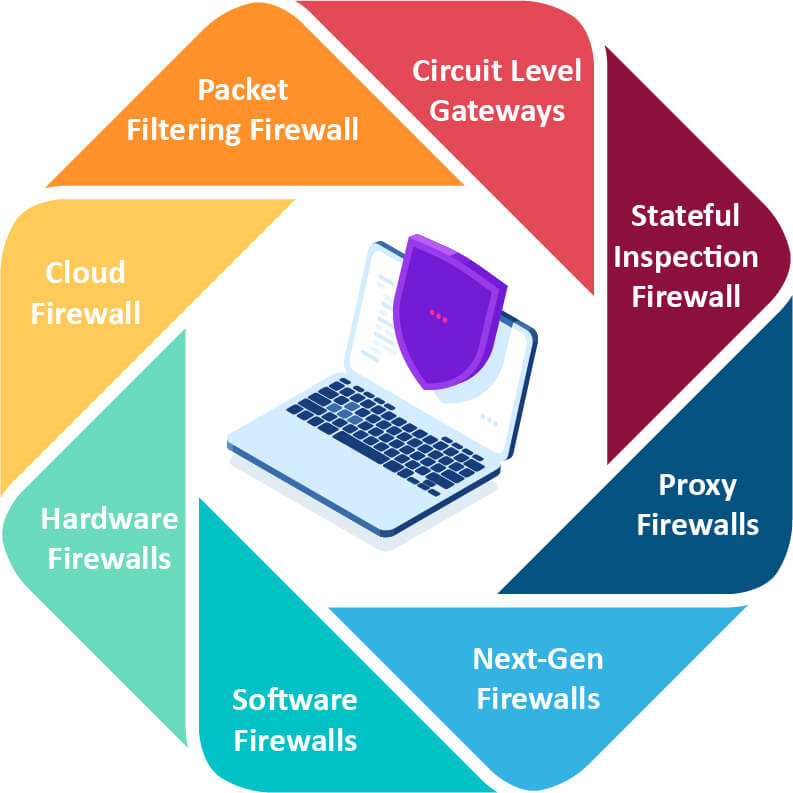
Packet Filtering Firewall
Packet filtering firewall is the oldest type of firewall architecture. It creates a checkpoint at the traffic router or switch and performs a simple check of the data packets coming through the network. If a packet doesn’t pass the inspection, the firewall drops the packet.
Circuit Level Gateway
Circuit level gateway is another simple firewall architecture that verifies the Transmission Control Protocol (TCP) handshakes. It doesn’t consume significant computing resources. In some extreme-resource conditions, it doesn’t check the packet itself. So if a packet holds malware and has an unsuspicious TCP handshake, it allows the packet to pass through the network.
Stateful Inspection Firewall
Stateful Inspection Firewall combines the packet filtering firewall and circuit-level gateways. So, it has the capability to check both the packets and TCP handshakes. However, this type of firewall stresses the computing resources as it requires significant computing power.
Proxy Firewall
Proxy Firewall filters the application traffic between the network and the traffic source by operating at the application level. For this functionality, it is also called an application-level gateway. This type of firewall can be delivered via a cloud-based solution or a proxy device.
Next-Gen Firewall
The recently-released firewalls are touted as Next-Gen Firewalls with deep-packet inspection, TCP handshake checks, and surface-level packet inspection. They are bolstered with Intrusion Prevention System (IPS) to automatically stop unauthorized intrusions.
Software Firewall
Rather than a separate piece of hardware, software firewalls installed in the local device. It can isolate the individual endpoints from one another and creates an in-depth defense. However, it is time-consuming to maintain individual firewalls on different devices.
Hardware Firewall
A hardware firewall is a physical appliance that inspects the data packets passing through the network. It is widely used for perimeter security to filter malicious traffic originated from outside the organization.
Cloud Firewall
A cloud solution used to deliver a firewall is called a cloud firewall or firewall-as-a-service. It is easy to scale based on the requirement of the organization. As the need grows, additional capabilities can be added to address the emerging threats.
Limitation of Firewalls
Though the firewall has an undeniable advantage in defending the network from cyber threats, as organizations are increasingly connected to outside security perimeter, the increasing traffic flow from the internet posing challenges to the firewall to handle packets in a short span.
Firewall Penetration Testing Methodologies
Firewall penetration testing is structured as indirect information collection, direct information collection, insider attacks, and outsider attacks.

Indirect Information Collection
Penetration Testers use publicly available information to collect data in a way that cannot be detected by any logging or alarming systems. They use penetration testing tools such as nslookup and whois to get ideas about the structure of the targeted network.
Direct Information Collection
Penetration testers look for additional information such as the organization’s name server which usually stored on the network topology. Some data can be collected from the header of bounced emails. For other information, they use automated tools like SATAN.
Outsider Attacks
Penetration testers target both the firewall and other designated systems like WWW servers or hosts that have a connection with the outside world. It is an added advantage if the firewall trusts these servers and hosts.
Insider Attacks
Penetration testers target the vulnerability in the firewall or the operating systems to exploit using insider information. This type of testing not only belongs to the network security but also to the host security. The testers use OS vulnerability tools like SATAN and ISS.
Report Key Findings of Firewall Penetration Testing

The key findings document should address the root cause of the weakness, test effectiveness, lessons learned through the process, and action plans. For any kind of firewall penetration testing, the penetration tester uses firewall data such as logs and weak spots. It is important to document all the inputs and findings from the testing. The documentation should include the method of attack used on the targeted firewall, the type of firewall, identified misconfigurations, and penetration testing tools. A qualified penetration testing service provider should estimate the business impact and provide recommended action plans to mitigate the risk.
Schedule a call to explore our Penetration Testing Services