Quick Summary: The article details common network security vulnerabilities, highlighting various threats like malware, unpatched systems, firewall misconfigurations and many more. It stresses the importance of continuous vigilance, regular updates, and educating employees to mitigate these risks. It also underscores the need for comprehensive security measures and cultural awareness within organizations.
Networks face constant threats from malicious actors seeking to exploit weaknesses in their architecture and implementation. From misconfigured firewalls to phishing attacks, vulnerabilities can leave sensitive data and critical systems exposed. Understanding these risks is the first step toward strengthening your security posture and building robust defenses to prevent breaches. This guide examines the most prevalent network security loopholes and offers practical approaches to mitigate these risks effectively.
What Are Network Vulnerabilities?
Network vulnerabilities are weaknesses within network systems that attackers can exploit to gain unauthorized access, disrupt operations, or extract valuable information. These security gaps may arise from hardware configurations, software implementations, weak security protocols, or result from human error. Addressing these vulnerabilities requires continuous attention through systematic updates, careful configuration management, and constant monitoring. Building a security-focused approach helps organizations identify and remediate potential entry points before attackers can leverage them.
Types of Network Vulnerabilities
Below listed are some critical network vulnerabilities that demand immediate attention from security professionals:
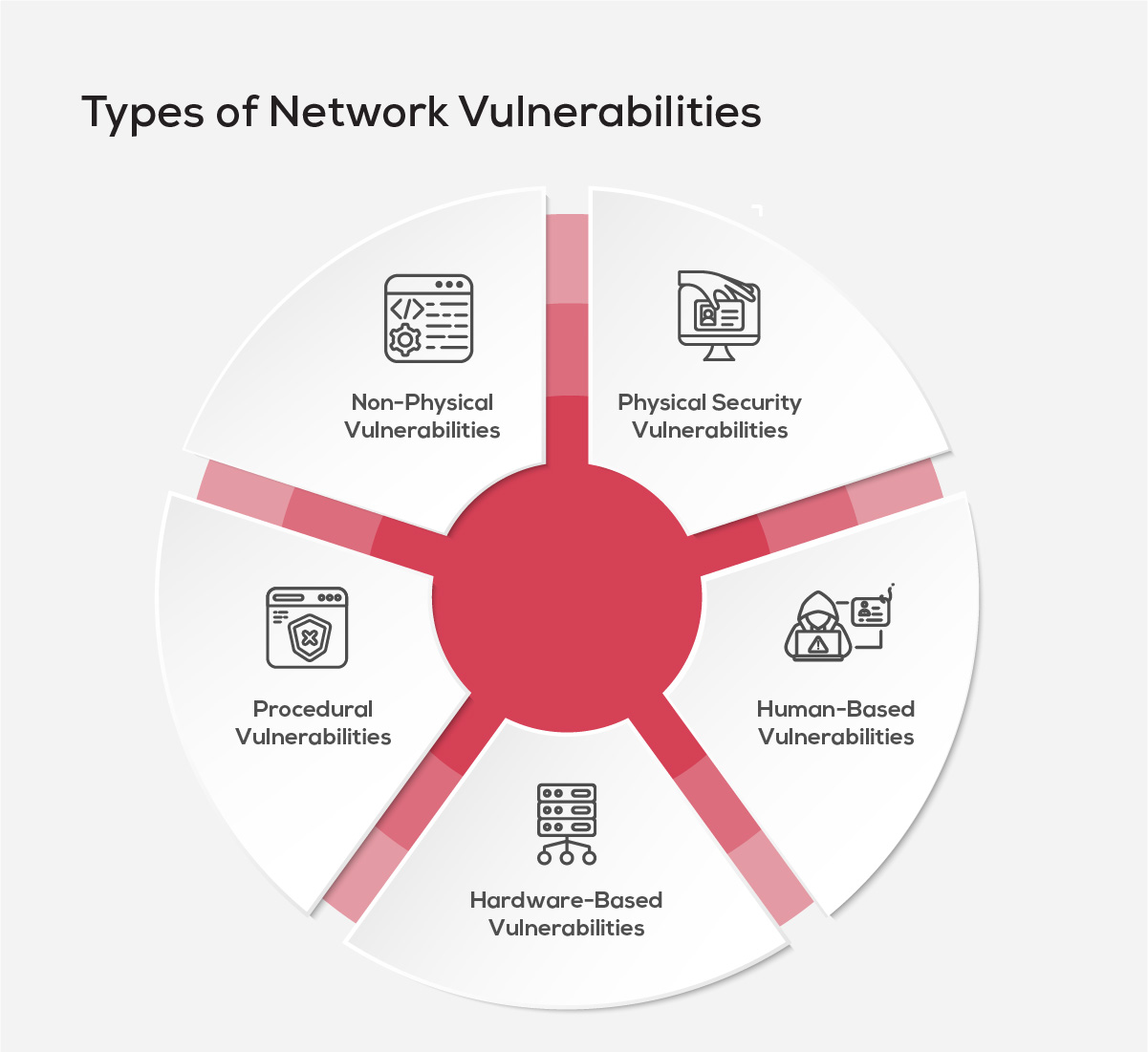
1. Non-Physical Vulnerabilities
Non-physical vulnerabilities refer to weaknesses in data, software, and digital systems that can be exploited without requiring physical access to network equipment. These vulnerabilities often serve as primary entry points for remote attackers. Addressing these vulnerabilities through regular updates, and proactive monitoring is crucial for minimizing risks.
Malware:
Malware is one of the most common threats to network security, exploiting systems through various types of viruses, worms, trojans, ransomware, and spyware, which are specifically designed to exploit network vulnerabilities.
Viruses attach themselves to authorized programs and spread when these programs execute. Worms can self-replicate and spread autonomously across networks without requiring user interaction. Trojans disguise themselves as legitimate software while performing harmful actions behind the scenes. Once installed, malware can establish backdoors, steal sensitive information, encrypt data for ransom, or grant attackers persistent control over compromised systems.
Unpatched and Outdated System:
Software that lacks security updates harbors known vulnerabilities actively targeted by attackers. These unpatched systems miss critical security fixes that address flaws discovered since their release.
Beyond the absence of feature enhancements, outdated software introduces multiple attack vectors, including privilege escalation, remote code execution, and data extraction through documented exploits that are widely available to malicious actors.
The risk intensifies when the vulnerable software plays a central role in network operations or handles sensitive information. In these cases, exploitation can lead to widespread system compromise, data theft, or the deployment of additional malicious tools across the network.
Firewall Misconfiguration:
Firewalls serve as primary network defenders, but their effectiveness depends entirely on proper configuration and maintenance. Incorrect implementation creates dangerous security gaps that attackers actively seek to discover and exploit.
Configuration problems arise from various sources: inappropriate initial setup, failure to update rules as network needs change, overly permissive settings, or misalignment between security policies and actual network requirements. These issues often stem from insufficient understanding of network traffic patterns or inadequate attention to changing threat landscapes.
The consequences of firewall configuration errors can be severe. Networks with improperly configured firewalls may expose open ports, allow traffic from malicious IP addresses, or permit unnecessary services to operate—providing attackers with direct entry points into the network, potentially leading to data breaches, unauthorized access or system disruptions.
Authentication Weaknesses:
Poor password practices represent a fundamental security flaw across many organizations. Easily guessed, commonly used, or recycled passwords provide attackers with straightforward paths to breach network defenses.
The problem compounds when users apply identical weak passwords across multiple platforms, turning a single breach into multiple compromises. Additionally, networks relying on outdated authentication systems lack crucial protections like multi-factor verification, strong encryption, and brute-force attack prevention.
These deficiencies create opportunities for credential theft through various techniques, from simple password guessing to sophisticated interception of authentication data, ultimately granting attackers’ credentialed access to protected resources.
2. Physical Security Vulnerabilities
Physical security vulnerabilities involve weaknesses in the protection of tangible network components and the facilities that house them. These risks stem from direct physical access or environmental factors that can damage or compromise equipment. While digital security receive significant attention, inadequate physical security can undermine even the most sophisticated technical controls, as attackers with physical access can bypass logical security controls. Organizations must consider physical security as a fundamental layer in their overall security architecture to prevent attackers from simply walking through unlocked doors to access sensitive systems.
Unsecured Network Access Points
Inadequately secured network access points create direct pathways for unauthorized network users. Open or poorly protected wireless networks, misconfigured VPNs, and unmonitored remote access solutions all represent significant security liabilities.
These vulnerabilities become particularly dangerous in environments with minimal wireless security enforcement or loose guest network policies. Without proper authentication and encryption, these access points allow attackers to intercept network traffic, inject malicious code, or gain direct network access.
A notable example is the 2014 Target Corporation breach, where attackers exploited a weakly secured HVAC system connection to infiltrate the network. This breach resulted in the theft of financial data from approximately 40 million customers, demonstrating how a single unsecured access point can compromise an entire enterprise.
Physical Access Controls
Insufficient controls on physical access to network equipment and facilities create vulnerabilities to direct tampering, system compromise or data theft. Server rooms, network closets, and areas containing critical infrastructure require robust physical security measures to prevent direct access by unauthorized individuals.
A comprehensive physical security strategy includes multiple layers of protection, such as:
- Advanced access control systems using biometric authentication (fingerprint, retinal, or facial recognition)
- Key card or RFID badge systems with unique identification for each user
- Security cameras and motion detection systems
- Mantraps or security vestibules to prevent unauthorized entry through tailgating
- Physical locks on server racks and equipment cabinets
Organizations that store particularly sensitive data or manage critical infrastructure should implement these measures to prevent unauthorized physical access, which could lead to data theft or system compromise. Without proper physical security, even the strongest digital defenses can be rendered ineffective.
Environmental Threats
Network infrastructure faces risks from environmental factors such as power fluctuations, temperature extremes, water damage, or fire. Without proper environmental controls and backup systems, these physical threats can cause service disruptions or permanent data loss.
3. Human-Based Vulnerabilities
Human-based vulnerabilities arise at the intersection of technology and human behavior, where security breaches occur due to the actions, decisions, or manipulations of people rather than technical flaws in systems. These vulnerabilities are particularly challenging because they exploit fundamental human psychological tendencies—trust, helpfulness, fear, and urgency—that override technical security measures. Despite advances in technical security controls, human vulnerabilities remain among the most exploited attack vectors, offering attackers the paths of least resistance around otherwise robust defenses.
Social Engineering and Phishing Attacks
Phishing and social engineering attacks exploit human psychology rather than technical vulnerabilities, making them a major threat to network security. These deceptive tactics manipulate employees and users into revealing sensitive information or performing actions that compromise security.
Attackers craft themselves as trustworthy sources through emails, messages, or phone calls that appear to come from legitimate sources. They create urgency or trust to extract credentials, financial details, or system access information from unsuspecting victims.
With the rise of generative AI, phishing and social engineering tactics have become more sophisticated and harder to detect, making proactive security awareness training essential.
Insider Threats
Internal security threats present unique challenges because they originate from individuals who already possess authorized network access. Whether intentional or accidental these threats can cause substantial damage that bypasses traditional security controls.
Detecting insider threats is particularly challenging due to the legitimate permissions these individuals hold. Employees, contractors, and partners with authorized system access can misappropriate data, leak confidential information, sabotage systems, or facilitate external attacks without triggering typical security alarms.
Addressing these threats requires advanced monitoring systems that can identify abnormal behavior patterns even when performed using legitimate credentials. Additionally, implementing strict access controls, security awareness training, and a zero-trust approach can help minimize risks. Without such capabilities, organizations remain vulnerable to threats that materialize from within their security perimeter.
Poor Security Awareness
Lack of security training and awareness among staff members creates significant vulnerabilities. When users lack understanding of basic security practices—such as identifying phishing attempts, managing passwords properly, or neglecting security protocols, they inadvertently create entry points for attackers. Strengthening security awareness through regular training and clear policies is essential to mitigating these risks.
4. Hardware-Based Vulnerabilities
Hardware-based vulnerabilities stem from weaknesses in physical devices that connect to or comprise the network infrastructure. Unlike software vulnerabilities that can often be addressed through patches and updates, mitigating hardware vulnerabilities may require physical replacement, reconfiguration, or additional security controls. These vulnerabilities pose a significant risk because they can provide persistent network access, bypassing software-based defenses. Inadequate hardware monitoring can further extend the risk, allowing these threats to go undetected for long periods.
IoT Vulnerabilities
The integration of IoT devices into networks has created substantial new attack surfaces with unique security challenges. These connected devices—ranging from environmental sensors to industrial controllers—frequently lack robust security architecture and implementation.
Common IoT security problems include factory-default credentials that remain unchanged, minimal built-in security controls, infrequent (or non-existent) security updates, and limited encryption capabilities. Each of these shortcomings provides potential entry points for network attackers.
The 2016 Mirai botnet incident demonstrated the scale of this threat when attackers compromised thousands of IoT devices and coordinated them to launch massive distributed denial-of-service (DDoS) attacks against internet infrastructure. This incident highlighted how unaddressed security flaws can turn vulnerable devices into weapons, causing widespread service disruptions.
Unsecured Network Equipment
Network infrastructure components like routers, switches, and access points can introduce significant vulnerabilities when improperly secured. Default administrative credentials, outdated firmware, and misconfigured settings on these devices create critical security gaps, potentially exposing networks to unauthorized access and cyber threats.
Physical Hardware Tampering
Direct physical access to network equipment creates opportunities for hardware-based attacks. Unauthorized devices connected to network ports, rogue wireless access points, and tampering with existing equipment can all lead to security breaches that bypass software-based protections.
5. Procedural Vulnerabilities
Procedural vulnerabilities arise from inadequate or missing security processes, policies, and operational practices within an organization. Unlike technical vulnerabilities that cannot be addressed with patches or configuration changes, procedural vulnerabilities require improvements in organizational behavior, documentation, and consistent execution of security practices. These vulnerabilities often create systematic weaknesses that persist across the organization and can undermine otherwise strong technical security controls. Addressing procedural vulnerabilities requires organizational commitment to security governance and the implementation of consistent, documented security processes throughout the enterprise.
Insufficient Security Assessments
Organizations that neglect regular security evaluations remain dangerously unaware of weaknesses in their network defenses. Comprehensive audits provide critical visibility into vulnerabilities before attackers can discover and exploit them.
Effective security assessments systematically examine an organization's entire security posture—from technical infrastructure to policy implementation and user behavior. These assessments identify infrastructure weaknesses like unpatched systems and misconfigured equipment while also evaluating access control mechanisms, physical security measures, and incident response capabilities.
Regular security testing helps organizations maintain awareness of their defensive capabilities and vulnerabilities as both their networks and threat landscapes evolve. Without this ongoing assessment process, security gaps may remain undetected until after exploitation occurs, significantly increasing damage potential.
Inadequate Backup Procedures
Failure to maintain current, tested backups of critical systems and data creates significant vulnerability to ransomware attacks, data corruption, or system failures. Without a reliable backup procedures, organizations risk permanent data loss or extended operational disruptions following security incidents.
Insufficient Incident Response Planning
Organizations without well-defined incident response procedures face increased damage when security breaches occur. The absence of clear protocols for detecting, containing, eradicating, and recovering from security incidents extends the impact of successful attacks and increases recovery costs.
Consequences of Inadequate Security
The failure to address these vulnerabilities can lead to severe impacts on organizations:
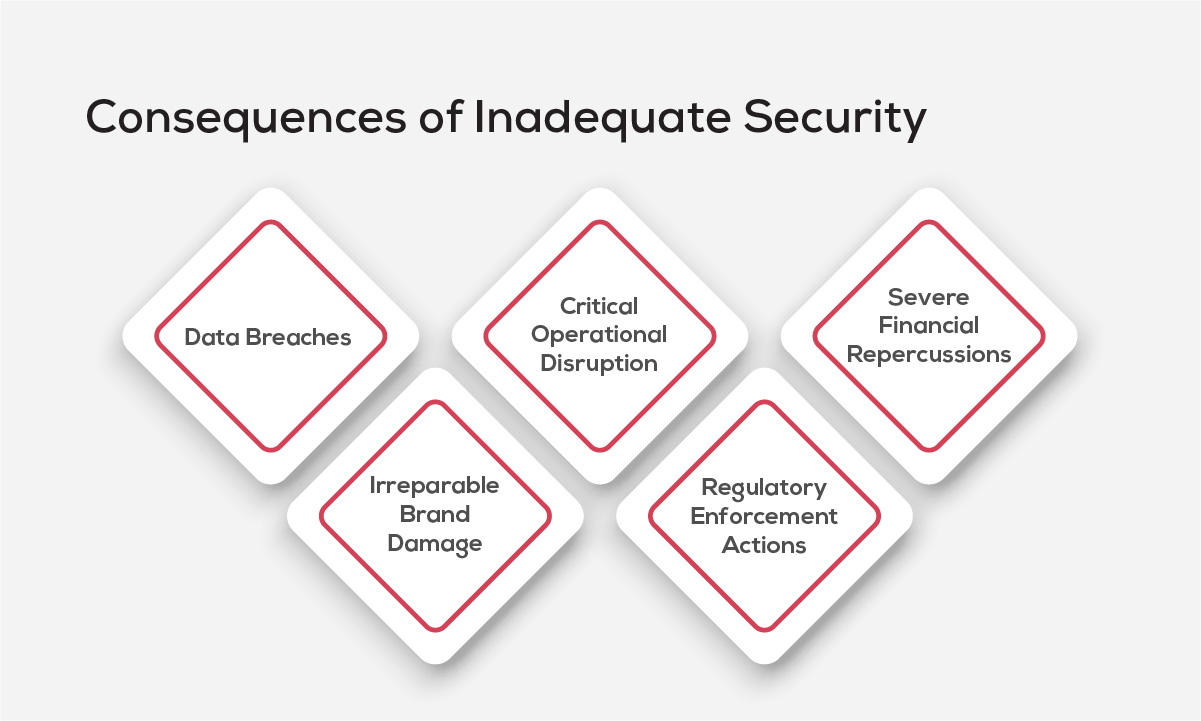
- Data Breaches
When security settings are improperly configured, sensitive data becomes exposed to unauthorized access. Attackers exploit these gaps to extract valuable information including customer records, proprietary data, and financial details potentially leading to financial losses and reputational damage. Ensuring proper security configurations is crucial to preventing such breaches.
- Critical Operational Disruption
Beyond data theft, security misconfigurations can compromise system integrity, leading to service outages, corrupted databases, and lost intellectual property. These disruptions not only halt business processes, but also create recovery backlogs, and damage customer relationships.
- Severe Financial Repercussions
Financial repercussions from data breaches can be devastating, including legal fines up to 4% of global revenue, heightened insurance premiums, and significant losses from customer churn and missed opportunities. Additional costs also cover forensic investigations, customer notifications, and legal defenses against lawsuits.
- Irreparable Brand Damage
Trust, once broken, proves extremely difficult to rebuild. Public perception shifts dramatically following security incidents, with studies showing 65% of consumers reconsider doing business with companies following a breach. This erosion of trust directly affects customer acquisition, retention, and partnership opportunities.
- Regulatory Enforcement Actions
As accountability tightens, organizations face severe consequences for security lapses, including forced audits, operational constraints, and substantial financial penalties, placing both executives and operations at risk.
Even minor misconfigurations can set off a chain reaction of security failures, leading to severe organizational consequences. This underscores the vital need for comprehensive network security management.
List of Network Security Measures
Explore essential network security measures designed to safeguard your digital infrastructure from unauthorized access and cyber threats.
- Firewall Activation: Activating a firewall is a crucial first step in preventing unauthorized access. Windows and macOS come with built-in firewalls that filter data packets, blocking malicious traffic before it reaches your network. Ensure they are enabled before connecting to the internet to enhance security.
- Complex Passwords: Establish complex passwords and unique security question answers, employing strategies like translating them into other languages to enhance security. Consider using a password manager to securely store complex credentials.
- Antivirus Deployment: Deploy antivirus software to protect against viruses and malware, with systems like Bitdefender and Avast that continuously monitor and remove threats.
- Access Control Enforcement: Implement network access control to limit user access to necessary areas, enhancing overall security through methods like biometrics and security tokens.
- Policy Updates: Regularly update security policies to align with evolving business needs and ensure staff is aware of any changes. Conduct training sessions to keep employees informed and aligned with these updates.
- Anomaly Detection: Integrate machine learning-based anomaly detection to streamline system security by identifying and mitigating hard-to-spot outliers, strengthening system security against hidden threats.
- VPN Utilization: Secure online activity and enhance privacy with VPNs, encrypting data and shielding business operations from third-party snooping.
- Intrusion Prevention: Strengthen defenses with intrusion prevention systems that recognize signatures and anomalies, swiftly mitigating threats before they cause harm.
- Authentication Enhancement: Strengthen login security with multi-factor authentication, requiring additional verification steps like one-time codes or biometrics to protect user accounts.
- Security Training: Promote security awareness training to educate employees on maintaining strong password practices and recognizing phishing attempts, ensuring compliance with standards like HIPAA and GDPR.
Conclusion
Effective network security goes beyond deploying measures—it's about cultivating a culture of continuous improvement and awareness. As digital threats evolve, organizations must stay ahead by combining cutting-edge defenses with a proactive security mindset. This ongoing process enhances our ability to detect, mitigate risks, and defeat potential threats, securing not just our systems but also the critical data they support. By encouraging awareness and consistently updating security protocols, organizations can enhance their network defense against ever-evolving cyber threats.
Frequently Asked Questions
1. What do you mean by vulnerability?
A vulnerability refers to a weakness in a system that can be exploited by cyber threats to gain unauthorized access or cause harm.
2. What causes network vulnerabilities?
Network vulnerabilities can arise from software bugs, outdated systems, misconfigured hardware, weak security protocols, and human error.
3. What is a DDoS attack, and how does it exploit network vulnerabilities?
A Distributed Denial of Service (DDoS) attack floods a network with excessive traffic to overwhelm resources and disrupt service. It exploits network vulnerabilities by targeting insufficiently secured bandwidth and server capacities.
4. What is the role of a security information and event management (SIEM) system?
A SIEM system collects and analyzes security data from various sources within a network to detect unusual behavior, manage security events, and provide real-time security alerts for potential threats.
5. What is Zero-Day Vulnerability?
A zero-day vulnerability is a security flaw that is unknown to the software vendor and security community at the time of discovery. Since no patch or fix exists, attackers can exploit it before detection or mitigation measures are in place.